NITIИ.
Cyber Security professional.

Nitin D. Bangera
Always been a techy got my first PC when I was 14, scrambling with electronics is my hobby and breaking / fixing thing is part and parcel of a techy. Started my Cyber security journey when I was 29. Bug bounty and freelancing is where I started, then a corporate job changed the meaning of cyber security to me, sitting on the other side of the table showed me the whole picture of cyber security in an IT world. Lucky me, as the first org I work was a Unicorn In AI. The dynamic nature of the company with innovation are created on the fly, it’s a different challenge to keep up with AI tech and cloud services based application. Had also seen a ransomware and how an organization responds to it and recover from the incident within 15 days.
My Skills
RED teaming
Infra Security
Compliacne
Articles
DISCLAIMER!!! Below articles are not for the light hearted who follow the checklist of VAPT or compliance. 
"Checklist"
It is good to have a checklist to be in uniform, in a corporate and get complaint and put up a badge of the stander. A checklist is always created with a date; you might miss some test on a target that an update might have given to a tool, or a software used in the infra structure. This checklist was made by a person who tested the environment in the past. There is also a possibility that it might have missed some test.
The trend is to make more use of technology and stay up to date with the world. In an organization you will find yourself surrounded by tech, WIFI devices, TV, access barriers, Lan ports and many more. While testing you might test one device or an application but how about a relay of multiple application and devices?
e.g. Display is used to share a screen or show some content that an organization wants to show but there are 2 OS (Operating System) behind each display, an OS in a screen if it is a TV and an OS in the centralized controller behind the TV. Now if you can just plug in a WIFI ducky in the USB port of the TV you can exploit the vulnerability in the TV which is not connected to internet and never gets updated and send data to the controller behind via HDMI ARC, now that controller has an IP address which means it is connected to a DHCP server.
“Checklist is good, you can be unbelievable.”
"Trust but Verify"
In organization you might see there are documentation and processes that needs to be followed before any changes on the infrastructure has to be done. But there is a high chance that you might find some configuration open or not reverted after the upgrade or change done. These open doors might lead to entire infra compromise. Most of these critical changes are in IT changes like for troubleshooting tech team might create a local account with admin privileges but will forget to delete the account once the activity is completed.
Similar case where team kept folder of sales data accessible to everyone in the organization. Identifing it is simple, open SharePoint stared searching for random file name like resume pay-slip, month name, etc.
“Seeing the unseen”
In general, an evolving organization you might see the vendor count increasing for the tasks that was done on some excel sheet or to save cost. These vendors some time store sensitive data that we might feel not that important. That data can be new employee joining or security tool used in the organization, now both the data is sensitive. If data of employee is leaked who is been hired at a senior level then his designation can be used to send Smishing, vishing, etc. In organization there are process to perform due diligence, but are those done as per data severity?
We had a vendor from whom we have take a auctioning tool (PAAS) where different vendors places bid to fulfill the organizations requirement. The data stored in the tool might not be critical for any one how is not interested in the serving the organization. But vendors biding for same tender, this will be game changing. So while assessing the vendor we were playing with the page and found the signup page. We signed up with tempmail id’s and without verification account was created and we got access to their tool without subscription. This was very simple, and it was clear tool is not that strong in terms of security. But we were not ready what was next. To test further we created an account name “admin@vednor.com” as there was no mail verification we got the account with name admin and surprisingly it had admin rights to the portal now I was able to see all of the clients the vendor had on their portal all the open tender can add or delete anything on the portal.
“Devil is in the details ”
During COVID fastest way of transition from WFO to WFH was to move to Citrix and ask the user to use their personal system. To login to Citrix there is an agent installed on your system and you can login directly on the agent and it would open a window and then you can work on the VM hosted in the infra.
Now how to get data out of this containerized environment? I opened a document inside the VM and hit the print button, the normal function is to list the printers and drives inside the VM to print or save in PDF and printers connected inside the infra. When I clicked on save as PDF it showed me a window with my personal laptop drives, now I was able to save the data from secured remote server to my personal system at home. And there was no tracking of it. It might feel exporting data in PDF format might not impact so much, think if someone from sales is resigning and getting all the sales data or tender data out in pdf format.
Think of changing the extension of the file and getting it out.
“Recon is in the key” Getting access to Data center
Working in the head office has the benefit of having visibility to everything. In Small organization you might see security team works very closely with IT team, this helped me to get deep into the IT infra and all the tech implemented around. So, our DC has biometric and is centrally managed by an Admin team. I scanned the entire VLAN found all the devices and found the management portal, as this was managed by admin team It was obvious the password would be humanly guessable. And I got access to all the biometric data in the office. Now finding the data center biometric was to find the smallest list with IT team members. Now all I had to do is attach a USB fingerprint scanner to my system and add my fingerprint to the list.
As the attacks and hackers evolved the defenses have evolved as well. ZTNA (Zero Trust Network Access) This is a security solution that gives very granular control over each individual user’s laptop and list of access one user should have. Now a well configured secure laptop you will not have USB access, card reader, or creating a share folder, ZTNA last but not the least conditional access on corporate system.
Now how to compromise this network with no exit point. In August 2016 windows 10 got a feature of hosting a hotspot. Hotspot gave me a way point to connect my personal system to my corporate system. Soon I knew that what all network access (ZTNA) my corporate system had same was forwarded to my personal system, the first I did was try login in to corporate server I access to from my personal system and then I know I was able to login and also download data directly from server to my personal system and the logs generated on ZTNA was of my corporate system .
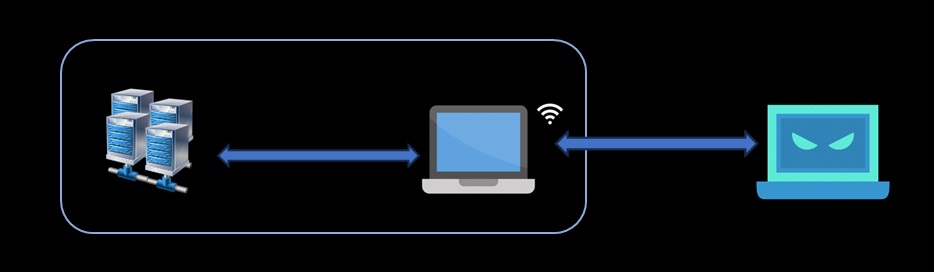
Imagin someone not so smart opens a hotspot without a password to share internet to his phone and forgets to turn it off.
“The closer you look the less you see" Web server on corporate laptop
Coding becoming DNA of most of the business sector analysis data is also done via python. Python has been a commonly known language for many domains for automations, you might find python by default installed on the corporate system. Now many of us know that python has a module of Simple.HttpServer which allows to host a web server on the system and you can download the files from a different laptop on the same local network.
To take it up by a notch, some broadband providers by default allows you to port forwarding on your router or you can ask for a port forwarding on nominal charge. All we have to do is add the inbound rule to the laptops IP address and we are live. All the secure data in a secure corporate laptop with 100’s of dollars of security tool installed is freely accessible on world wide web.
“Stay tuned for more......”
“All the above is just for educational purpose.”